History view
Cross-Site Scripting (XSS) vulnerability in Tistory edit post
theFaunia in the wild 2019. 12. 4. 20:50What is XSS?
Cross-Site Scripting (XSS) is probably the most common singular security vulnerability existing in web applications at large. It has been estimated that approximately 65% of websites are vulnerable to an XSS attack in some form, a statistic which should scare you as much as it does me.
XSS occurs when an attacker is capable of injecting a script, often Javascript, into the output of a web application in such a way that it is executed in the client browser. This ordinarily happens by locating a means of breaking out of a data context in HTML into a scripting context-usually by injecting new HTML, Javascript strings or CSS markup.
https://phpsecurity.readthedocs.io/en/latest/Cross-Site-Scripting-(XSS).html
Summary of vulnerability
There is XSS when a user edits a post from same blog and inserts a URL with an exploit for malicious purposes by executing Javascript code.
With this vulnerability you can:
- Steal session cookie from victim user if HttpOnly is not enabled.
- HTML inject for malware purpose (open redirection to evil.html).
- Phishing legit username and password from victim user.
This vulnerability affects at all blogs that use Tistory CMS.

Proof of Concept
We set the stage of exploitation being an attacking user and a victim user. Both users belong to a team with a blog together but the victim has other blogs belonging to other projects and the attacker does not have access to them.
The attacker through the vulnerability can steal the cookie from the victim's session and thus be able to use the account to see other blogs. (only can steal cookie session if HttpOnly is unset).
Another way of exploitation is to redirect the victim with HTML code injection using the vulnerability to visit a malicious website and download malware.
Step by Step :
- Create an exploit in other website for example using Tistory and write the following payload:

- In the common blog with the victim edit a post writing the malicious url and press enter:

- Share the URL edit post with the victim and wait for user click iteration and open redirection to evil.html website.
- With this poc we can execute Javascript code and inject HTML code for malicious purpose. For example redirect to evil.html and download backdoor malware.
We can see that the user if there isn't XSS exploitation, cannot visit the evil website:
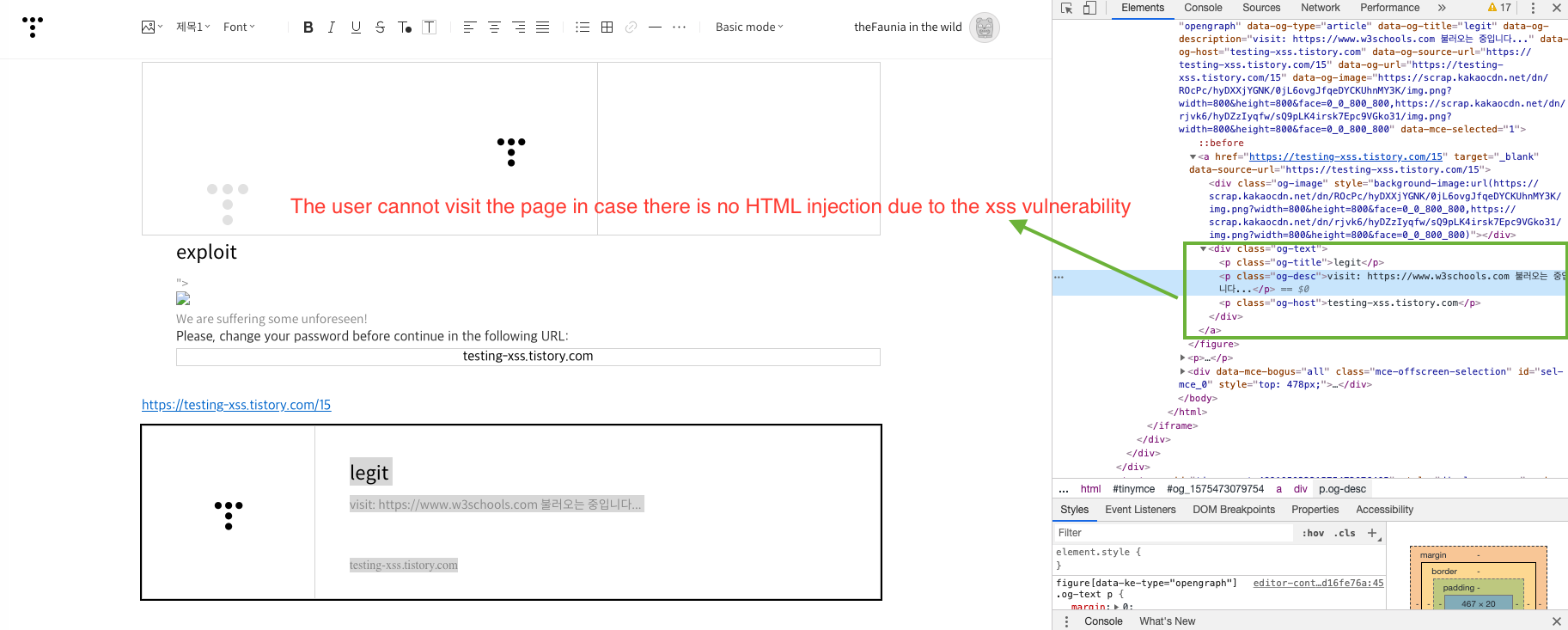
Happy hunting !.
- Total
- Today
- Yesterday
- use after free
- Windows
- cracking
- hijacking redirection flow
- XSS
- arithmetic overflow/underflow
- theFaunia course
- write primitive
- dnspy
- Pwnable.kr
- 32Bit
- buffer overflow
- open-redirect
- ASM
- leak libc
- return oriented programming
- canary
- x64dbg
- pwnable.xyz
- leak stack memory address
- pwnable.tw
- shellcode
- fake stack frame
- Backdoors
- Call oriented programming
- format string
- one gadget
- stack pivot
- GOT Dereferencing/Overwriting
- html injection
| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
